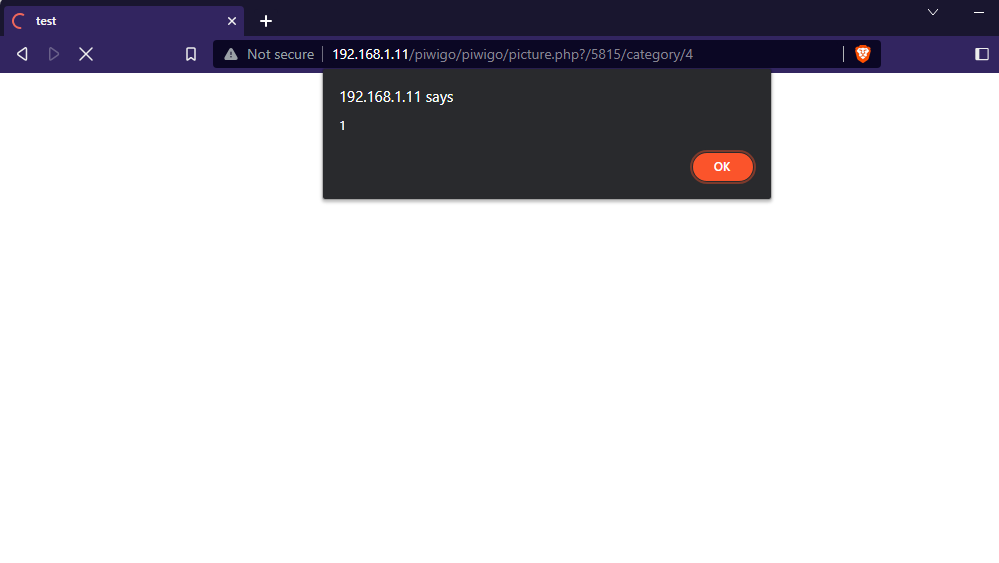
#Exploit Title: Piwigo v13.7.0 – Stored Cross-Site Scripting (XSS) (Authenticated)
#Date: 4 July 2023
#Exploit Author: Okan Kurtulus
#Vendor Homepage: https://piwigo.org
#Version: 13.7.0
#Tested on: Ubuntu 22.04
#CVE: N/A
#Proof of Concept:
1-) Install the system through the website and log in with any user authorized to upload photos.
2-) Click “Add” under “Photos” from the left menu.
3-) The photo you want to upload is selected and uploaded.
4-) Click on the uploaded photo and the photo editing screen opens. XSS payload is entered in the “Description” section on this screen.
Payload:
<sCriPt>alert(1);</sCriPt>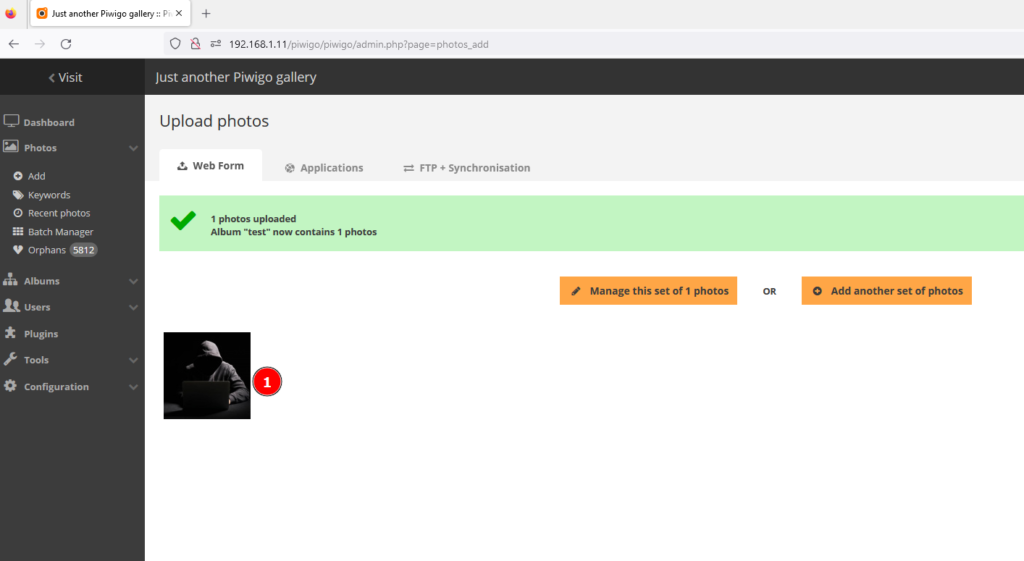
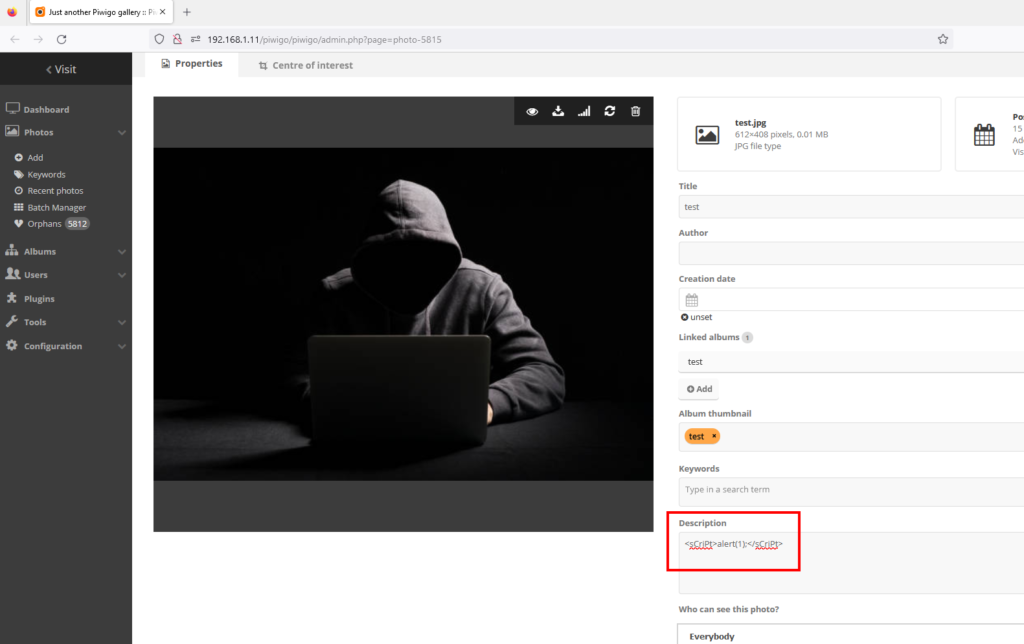
5-) After saving the file, go to the homepage and open the page with the photo. The XSS payload appears to be triggered.