Hi guys,
I am writing to report a potential Insecure Direct Object Reference (IDOR) vulnerability that I have discovered in KubeSphere. Below are the details of the vulnerability:
There is a potential Insecure Direct Object References (IDOR) vulnerability in KubeSphere which allows unauthorized users to access sensitive resources by manipulating object references. This issue can lead to unauthorized data exposure or modification without proper authorization checks.
CVE Number:
CVE-2024-46528
Affected Versions:
Both the open-source version of KubeSphere (kubesphere.io) and the Enterprise version (kubesphere.co) are affected by this vulnerability.
KubeSphere 4.x: < 4.1.3
KubeSphere 3.x: >= 3.0.0, <= 3.4.1
KubeSphere Enterprise 4.x: < 4.1.3
KubeSphere Enterprise 3.x: >= 3.0.0, <= 3.5.0
Vulnerability Verification Process:
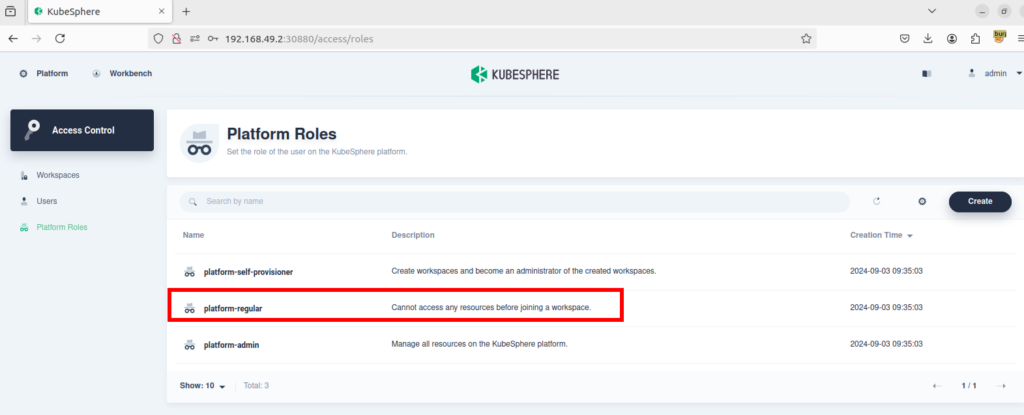
1-) When I checked the roles in the system, I noticed a role named “platform-regular.” The description for this role stated: “Cannot access any resources before joining a workspace.” This means that users with this role shouldn’t be able to access any resources unless they are part of a workspace.
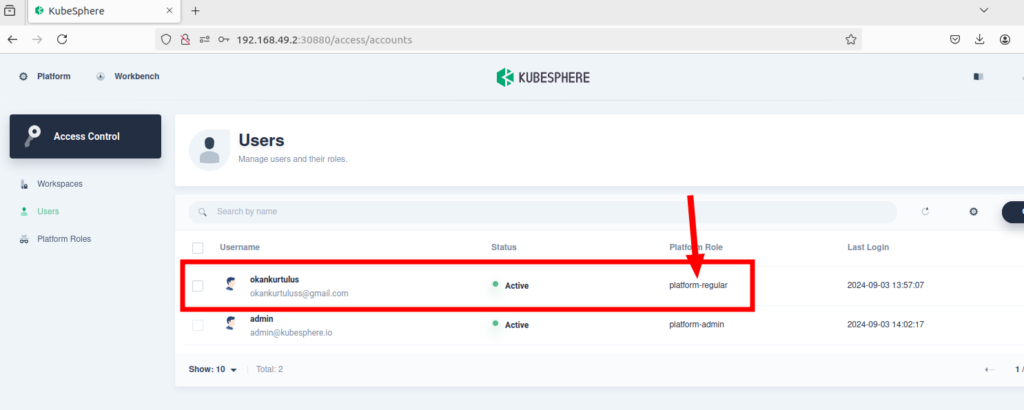
2-) I created a user named “okankurtulus” and assigned the “platform-regular” role to this user. This user does not have access to any workspaces.
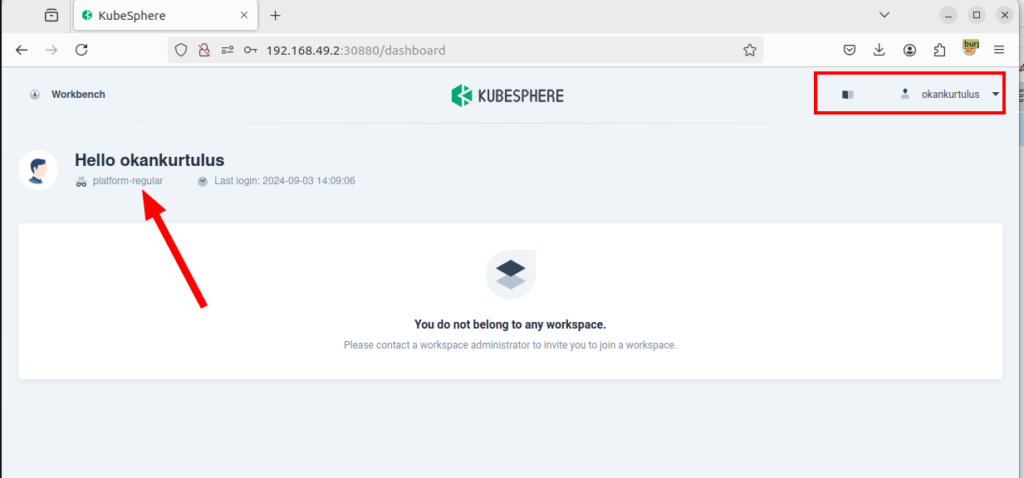
3-) However, despite not having access to any workspace, this user can access cluster resources, cluster nodes, registered users in the system, and other similar areas without having the necessary permissions.
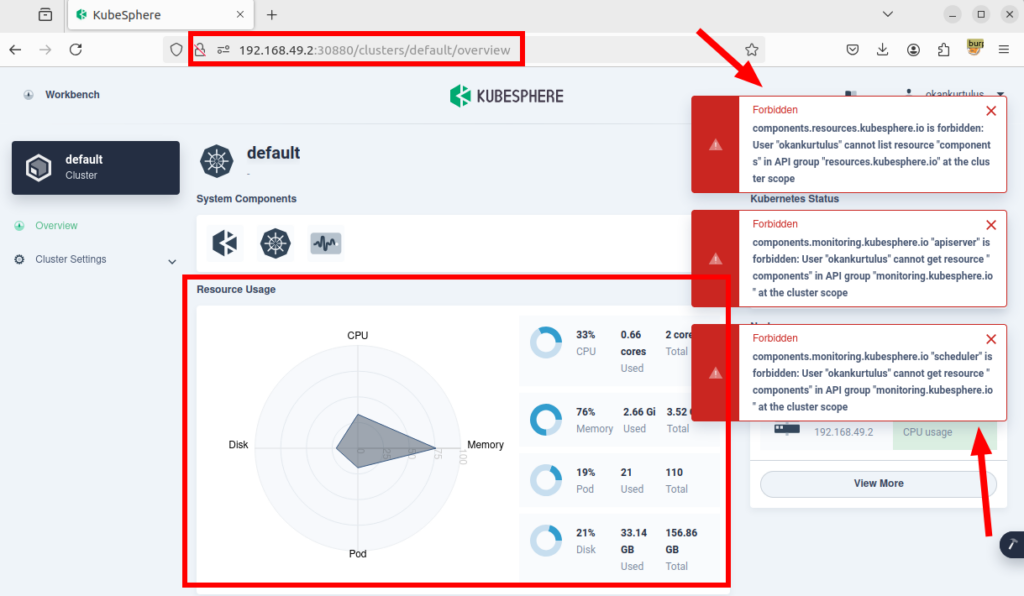
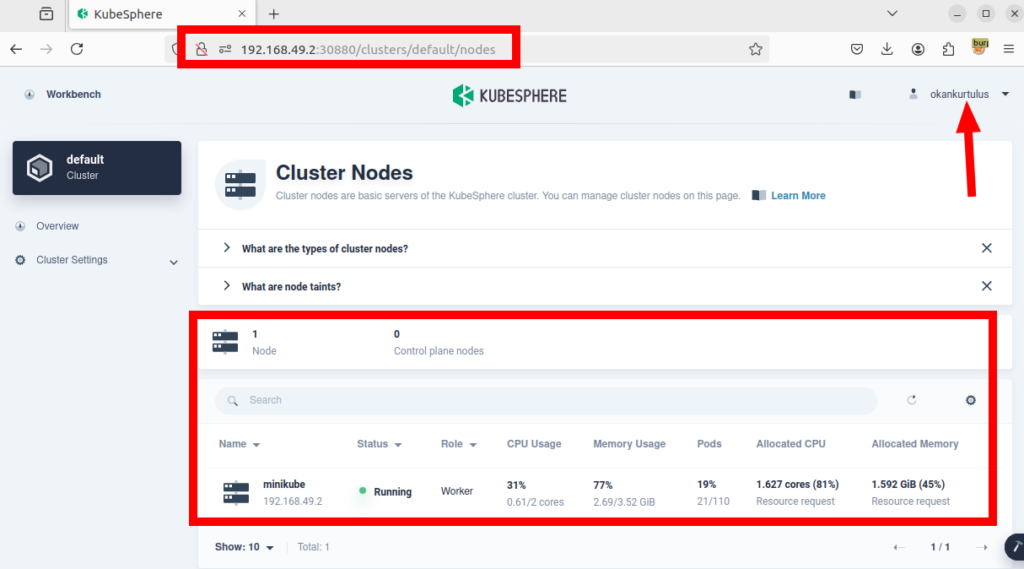
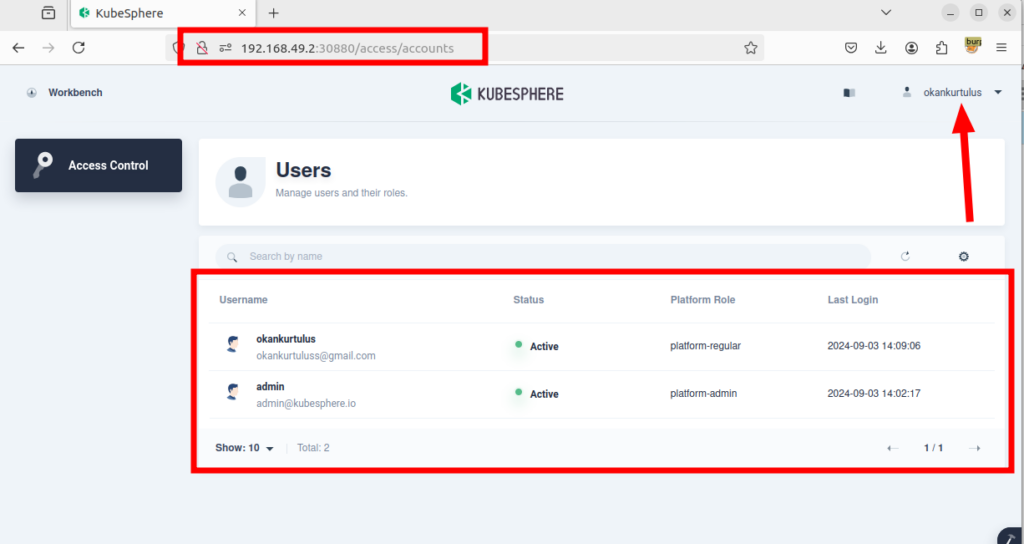

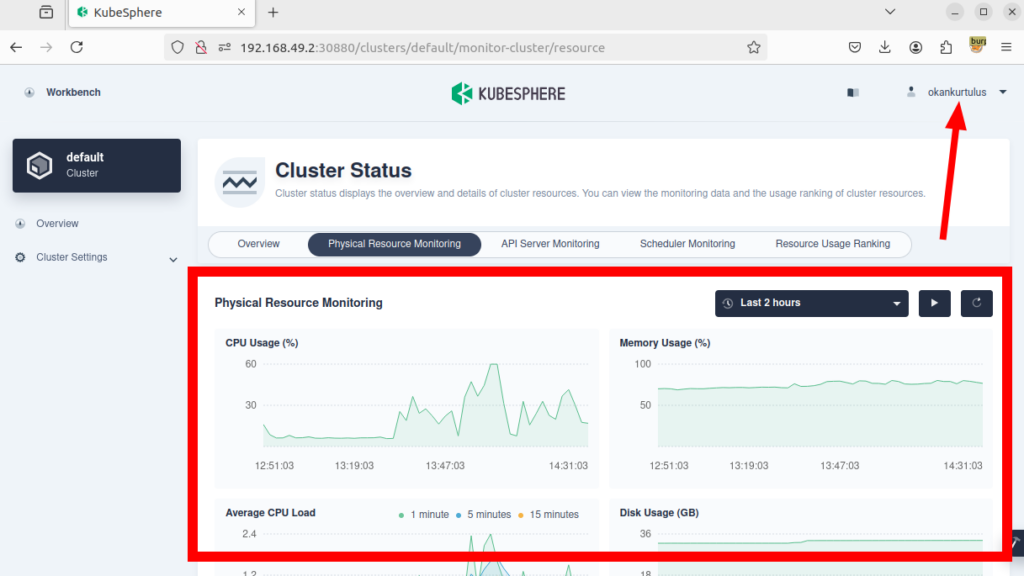
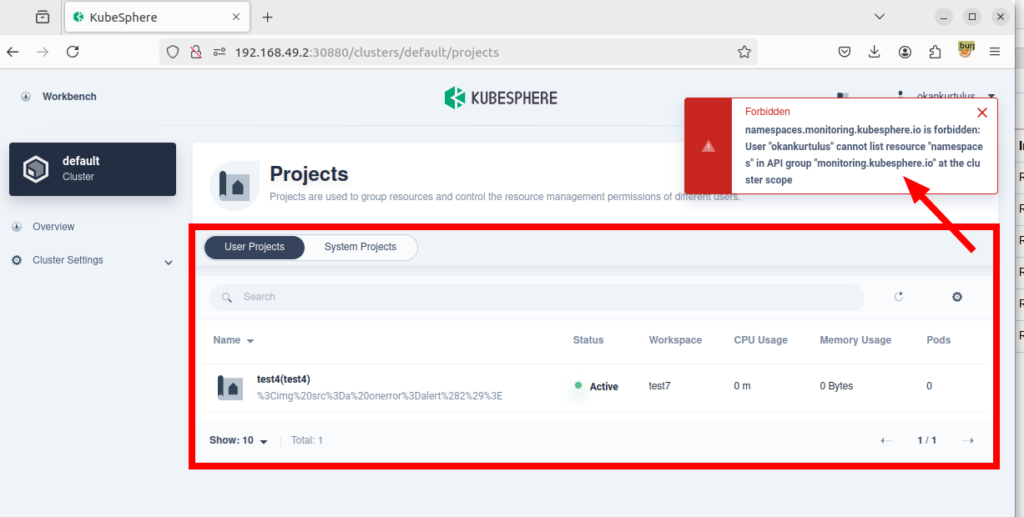
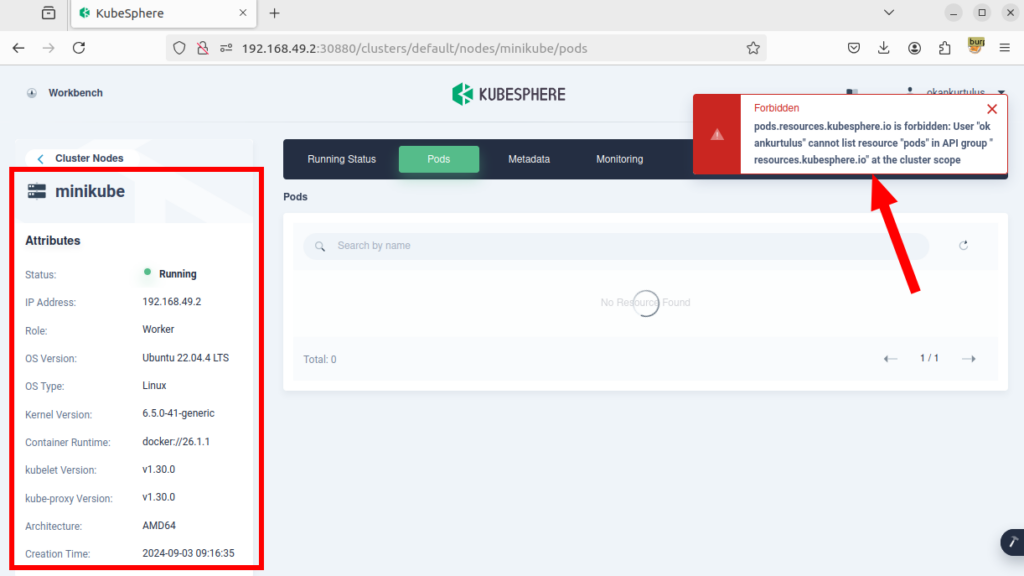
I have reported the vulnerability to the vendor. They responded quickly and provided a solution for the finding. If you upgrade to the latest version, you will not be affected by the vulnerability.
To mitigate the impact of this security vulnerability, you can implement the precautions recommended by the vendor.
